Hello amazing hacker, I am Deepak Dhiman a.k.a Virdoex_hunter from India. I hope you are doing well. I am a bug bounty hunter. So many people ask me how I use censys to find origin IP behind proxy waf such as akamai,cloudflare. So don’t waste time let’s start this.
If you don’t understand anything and want a detailed video on it please let me know via comments I will try to make it on my youtube.
 So their are two methods you can use censys for origin IP:
So their are two methods you can use censys for origin IP:
 STEPS 1:
STEPS 1:


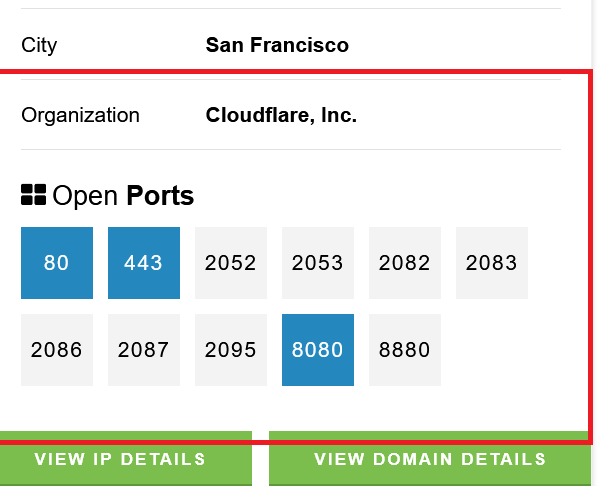
 So their are two methods you can use censys for origin IP:
So their are two methods you can use censys for origin IP:
- The hardest way(but little time saver)
- The easiest way( like a bluff that works).
 STEPS 1:
STEPS 1:
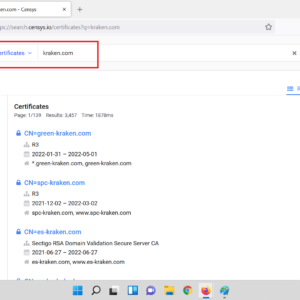
- Login to censys and go the censys search page choose certificates and in certificates search your target like this.

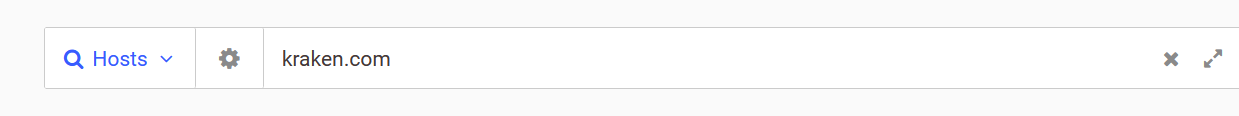
- Now open any certificate and in right you find Explore hover on it and click on hosts.

- Now in hosts copy every IP you found and try to open that in new tab.
EASY WAY : You wanna play Bluff I liked it.

- Login and this time put your target in hosts.

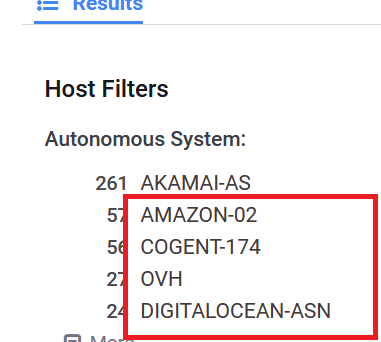
- Now choose other service Autonomous System rather then Cloudflare or Akamai .

- Try every IP in new tab and check autonomous IP but make sure cert.CN:must be target.com not anything else and also the target.com must to have in cert.CN: not in http.body or something else.
- So now you have IP that works and belong to target now how to make sure which domain it pointed too and either that domain is behind any WAF.
- grep all subdomain, resolve them using httpx or install multi url opener extension and shodan.io extension in browser.
- Paste all the urls and try to figure which clones or look like the ip url (front end) and if you find than on that domain tap on shodan extension to look wheather it is behind cloudflare or not like this.

- If yes than congratulation you find IP behind waf.
- Dirsearch
- Port scan
- test like the domain such as rate limit,xss ,2 fa bypass , password reset poisoning etc etc.